Security Testing (DAST)
Learn how to use AgentQ's Dynamic Application Security Testing (DAST) features to identify security vulnerabilities in your applications.
This feature is only available in the Enterprise version.
Overview
DAST (Dynamic Application Security Testing) helps you identify security vulnerabilities in your web applications by analyzing them while they're running. This automated security testing approach simulates real-world attacks to find potential security weaknesses.
Prerequisites
- AgentQ Enterprise account
- Test cases prepared for security testing
- Target application URL
Steps
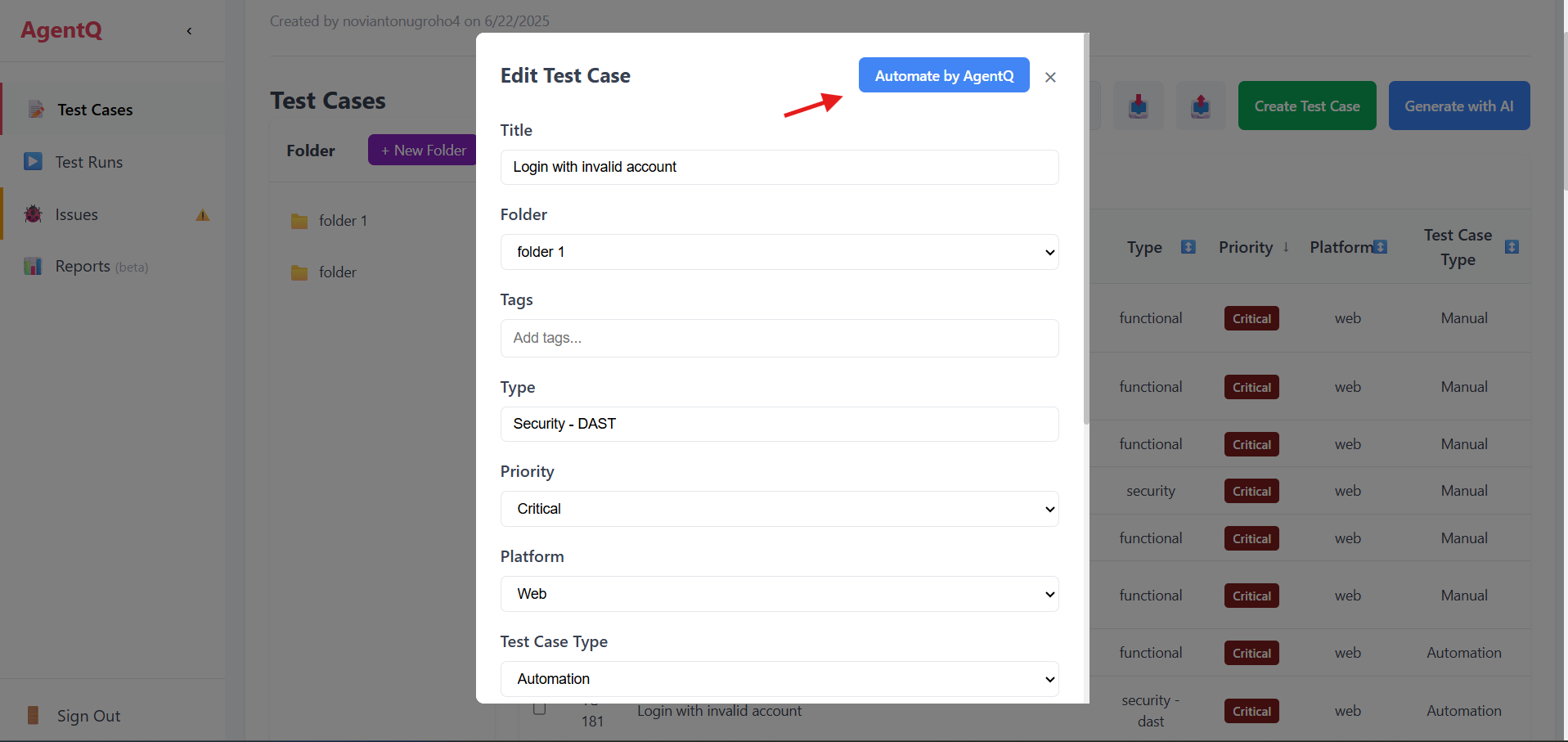
1. Start Automation
Click the "Automate by AgentQ" button to begin the security testing process.
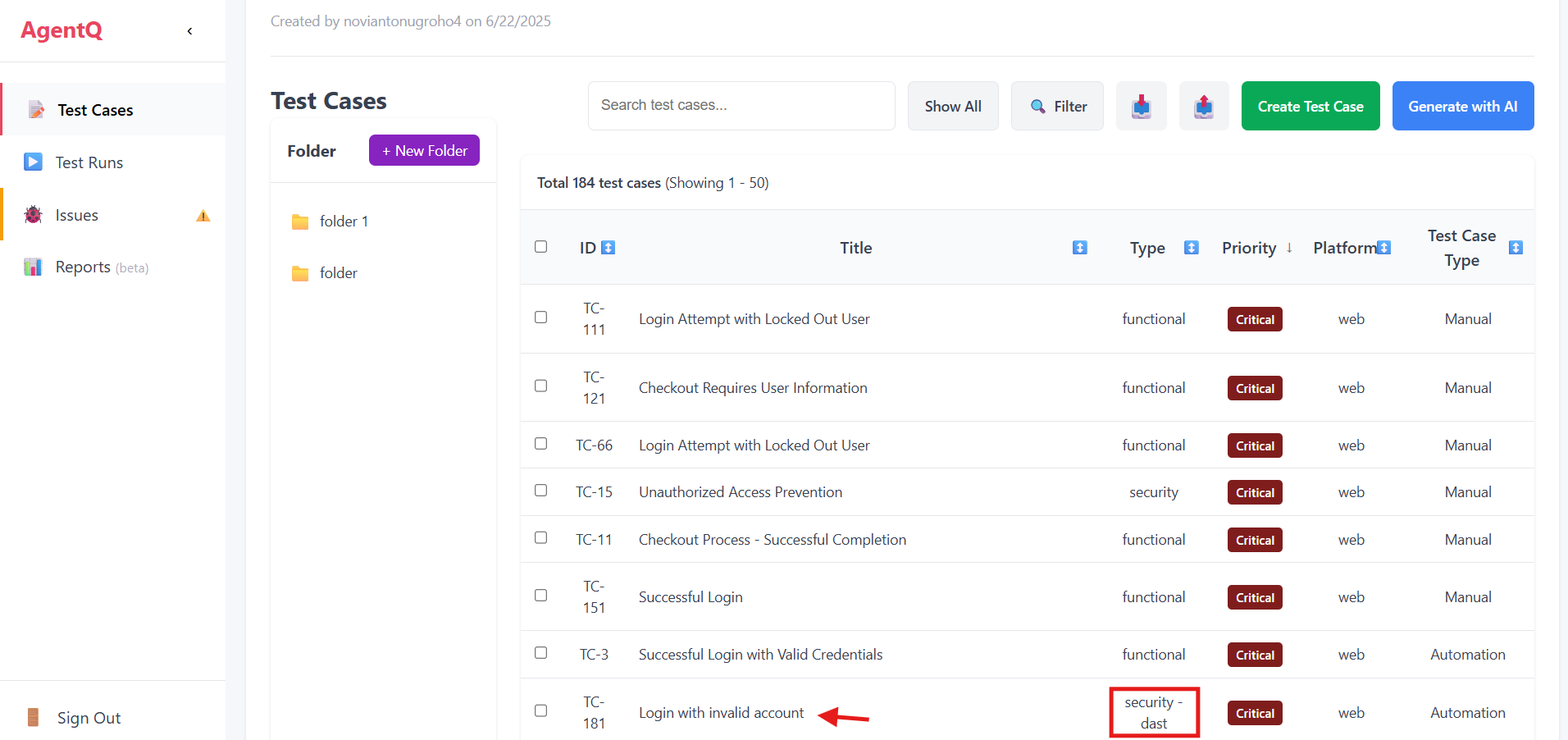
2. Select Test Case
Choose a test case that has been configured for security testing (type: security - DAST).
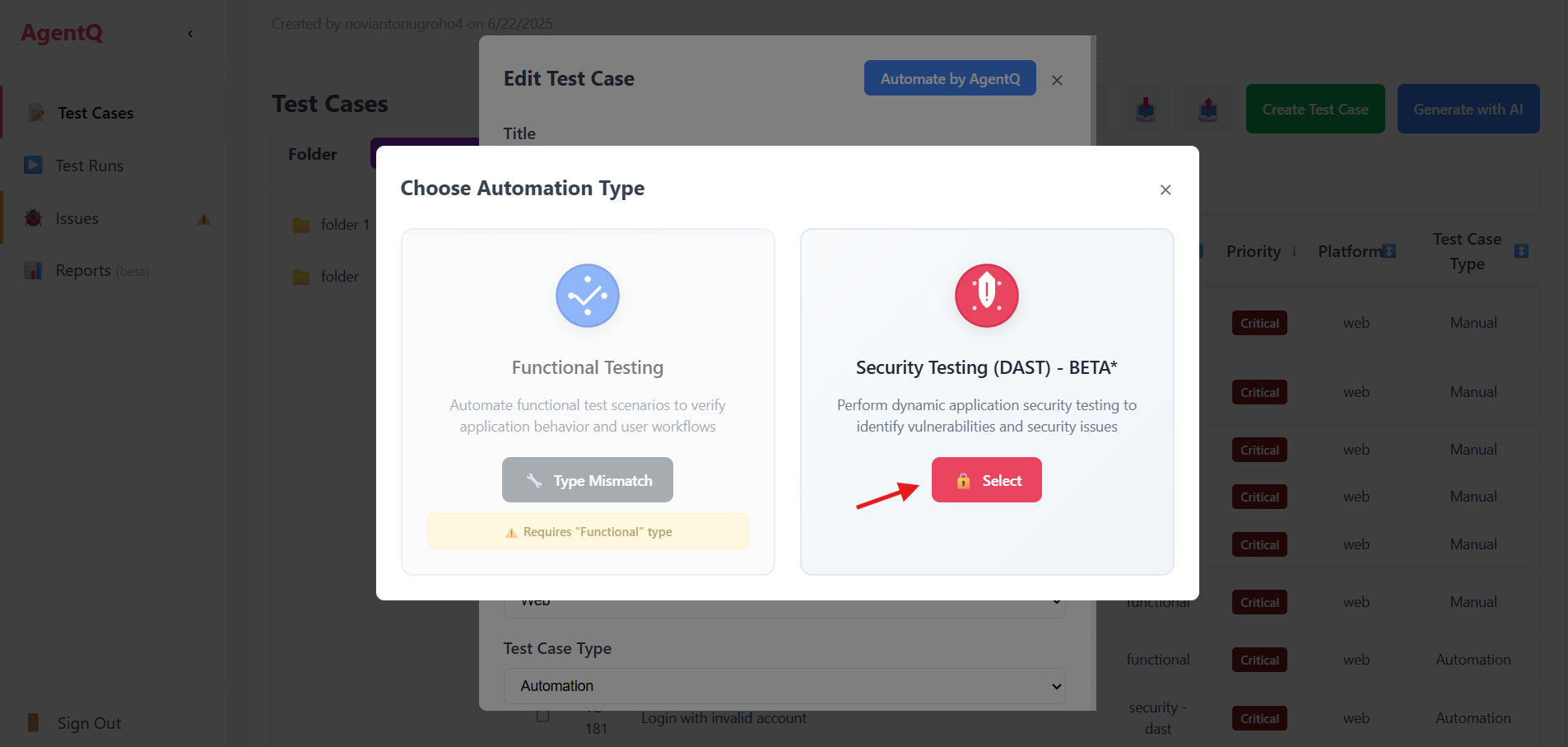
3. Select Test Type
Choose "Security DAST" from the available testing options.
4. Run Security Test
Click the "Run" button to start the security testing process.
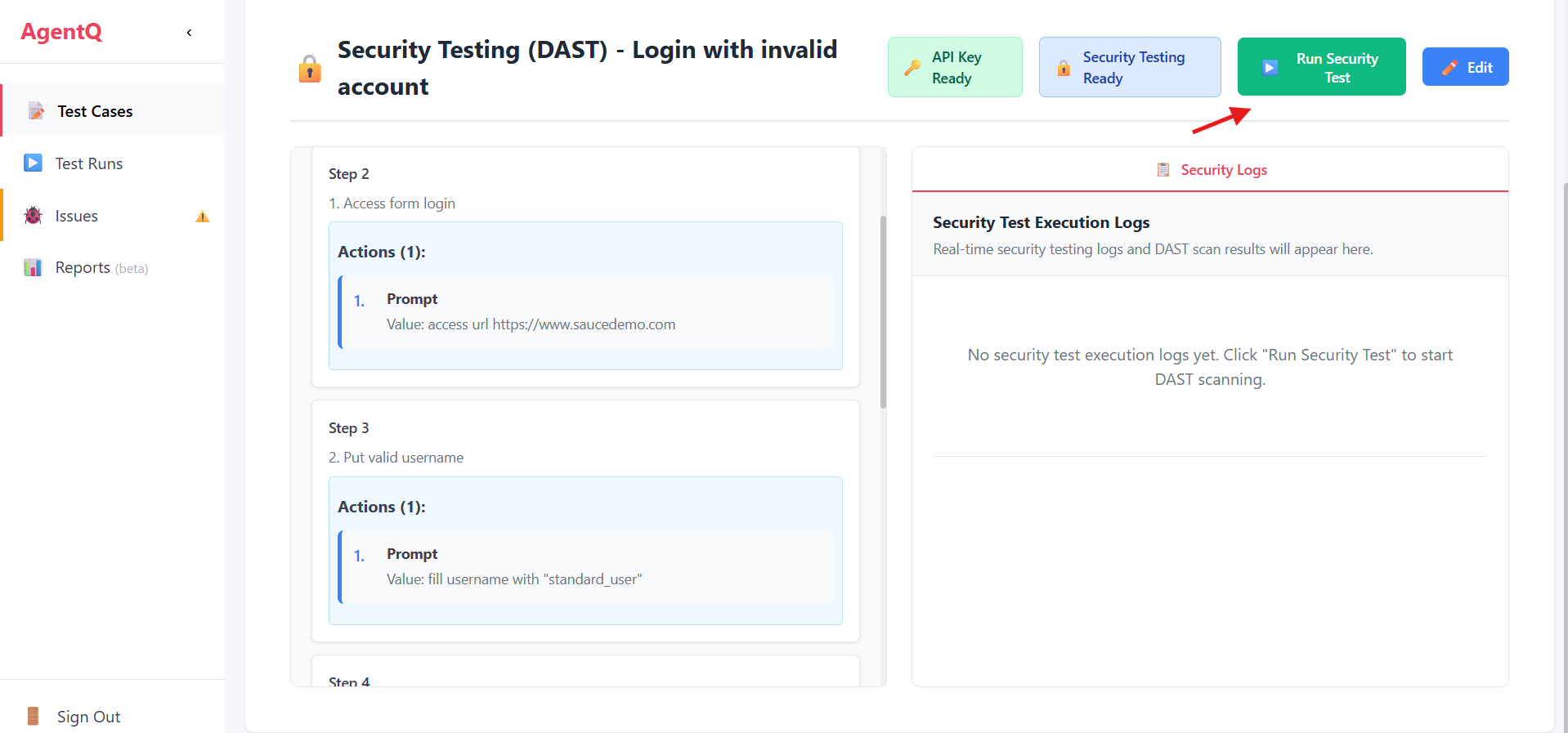
5. Monitor Testing Progress
The system will begin the security testing process. You can monitor the progress and view real-time logs of the security scan.
Key Features
- Automated vulnerability scanning
- Real-time testing logs
- Detailed security reports
- Multiple security test types
- Risk assessment and scoring
Best Practices
-
Test Planning
- Plan your security tests during off-peak hours
- Ensure you have proper authorization for testing
- Document all test scenarios
-
Test Configuration
- Use appropriate test cases for different security aspects
- Set proper scope for security scanning
- Configure authentication if required
-
Result Analysis
- Review all identified vulnerabilities
- Prioritize fixes based on risk levels
- Document and track remediation progress
Security Considerations
- Always obtain proper authorization before running security tests
- Monitor system performance during testing
- Follow security testing compliance requirements
- Keep security test results confidential
Troubleshooting
- If tests fail to start, verify your test case configuration
- Ensure target application is accessible
- Check network connectivity and firewall settings
- Verify authentication credentials if required